Key Components of ICS Security Include:
ICS security encompasses a range of practices and technologies designed to defend these systems from cyber threats to sustain industrial operations' integrity, availability, and safety. This doesn’t only help protect the digital systems themselves but also the physical infrastructure they control.
Industries Relying on ICS Security
- Energy and Utilities (power generation, water treatment)
- Manufacturing (automotive, food and beverage, pharmaceuticals)
- Transportation (railways, air traffic control)
- Oil and Gas (refineries, pipelines)
- Chemical Processing
- Mining and Metals
Importance of ICS Security
- Given the critical nature of the processes controlled by ICS, sustaining their security is paramount. A breach in an ICS could lead to:
- Production stoppages
- Equipment damage
- Environmental disasters
- Public safety risks
- Significant financial losses
Understanding the unique characteristics and requirements of Industrial Control Systems is crucial for developing effective ICS security strategies. As these systems become more connected and digitally dependent, the need for robust, specialized security measures becomes increasingly critical.
Examples of Real-World ICS Security Threats and Attacks
There were over 48,000 exposed ICS services in the US in 2024. An example of an ICS security attack over the last year is with the Cyber Army of Russia Reborn (CARR). This nation-state organization gained unauthorized access via Telegram, tampered with the HMIs, and overflowed water storage tanks in Muleshoe, Texas. Causing downtime and damage.
Why Do We Need ICS Security?
The need for robust ICS security has never been more critical. As industrial systems become increasingly connected to corporate networks and the internet, they’ve become attractive targets for cybercriminals and state-affiliated threat actors. Consider these alarming statistics:
Potential Consequences of ICS Breaches
The impact of a successful attack on an ICS can be severe and far-reaching:
- Safety Risks: In 2021, a hacker attempted to poison the water supply in Oldsmar, Florida, by increasing the levels of sodium hydroxide in the water treatment system. While this attempt was thwarted, it highlights the potential for physical harm to the public.
- Economic Losses: The 2017 NotPetya attack, which affected numerous companies including shipping giant Maersk, resulted in estimated global damages of $10 billion.
- Environmental Damage: In 2000, a disgruntled former employee hacked into the control systems of a sewage treatment plant in Maroochy Shire, Australia, causing millions of liters of raw sewage to spill into local parks and rivers.
- National Security Threats: The 2015 attack on Ukraine’s power grid, attributed to Russian hackers, left 230,000 people without electricity for up to six hours, demonstrating the potential for ICS attacks to disrupt critical national infrastructure.
- Reputational Damage: In 2014, a German steel mill suffered significant damage when a cyberattack prevented the proper shutdown of a blast furnace. Beyond the immediate physical and financial impact, such incidents can severely damage a company’s reputation and customer trust.
These examples underscore the critical need for robust ICS security measures. As industrial systems become more interconnected and digitally dependent, the potential consequences of breaches grow more severe, making ICS security an imperative for organizations across all industrial sectors.
Financial Impact of Breaches in ICS Security
The Cyber Threat Snapshot from the Committee of Homeland Security revealed that the average cost of a data breach in the US was $9.36 million—nearly double the global average.
Downtime is critical for businesses but can vary by industry. According to a recent study, Manufacturing spaces could be upwards of $260,000 per hour. Here are three key ways that you can calculate downtime based on industry:
- Manufacturing downtime = (Hourly labor cost + hourly overhead cost + hourly production cost) x downtime duration
- Wastewater treatment downtime = (Regulatory fines + environmental cleanup costs + labor costs + equipment repair/replacement + potential public health costs)
- Energy downtime = (Lost electricity sales + equipment repair/replacement + labor costs + regulatory fines + potential safety/environment costs)
Demonstrating ROI of Security Investments
While security is an investment, there are a few trackable metrics that can help you demonstrate ROI to your stakeholders:
- Reduction in Security Incidents: Monitor the number of successful and attempted cyberattacks, malware infections, and unauthorized access attempts.
- Improved Uptime: Track the percentage of uptime for critical systems and measure the reduction in unplanned downtime.
- Compliance with Regulations: Document compliance with industry standards and regulations to avoid fines and demonstrate due diligence.
- Risk Reduction: While difficult to quantify directly, emphasize the value of reducing the likelihood and impact of potential breaches. Use risk assessment frameworks to demonstrate the decrease in risk exposure.
How to Address Fear of Disrupting Critical Processes
Security doesn't have to mean downtime. There are a few ways to implement security measures strategically to help minimize disruption:
- Roll out security controls in phases based on priority from your OT security team
- Use virtual patching or compensating controls to address vulnerabilities without taking systems offline.
- Divide the network into isolated segments to limit the impact of the breach
- Implement backup systems to take over if one system needs to go offline
- Align your testing and update with the operations teams so there is no conflict with required uptime
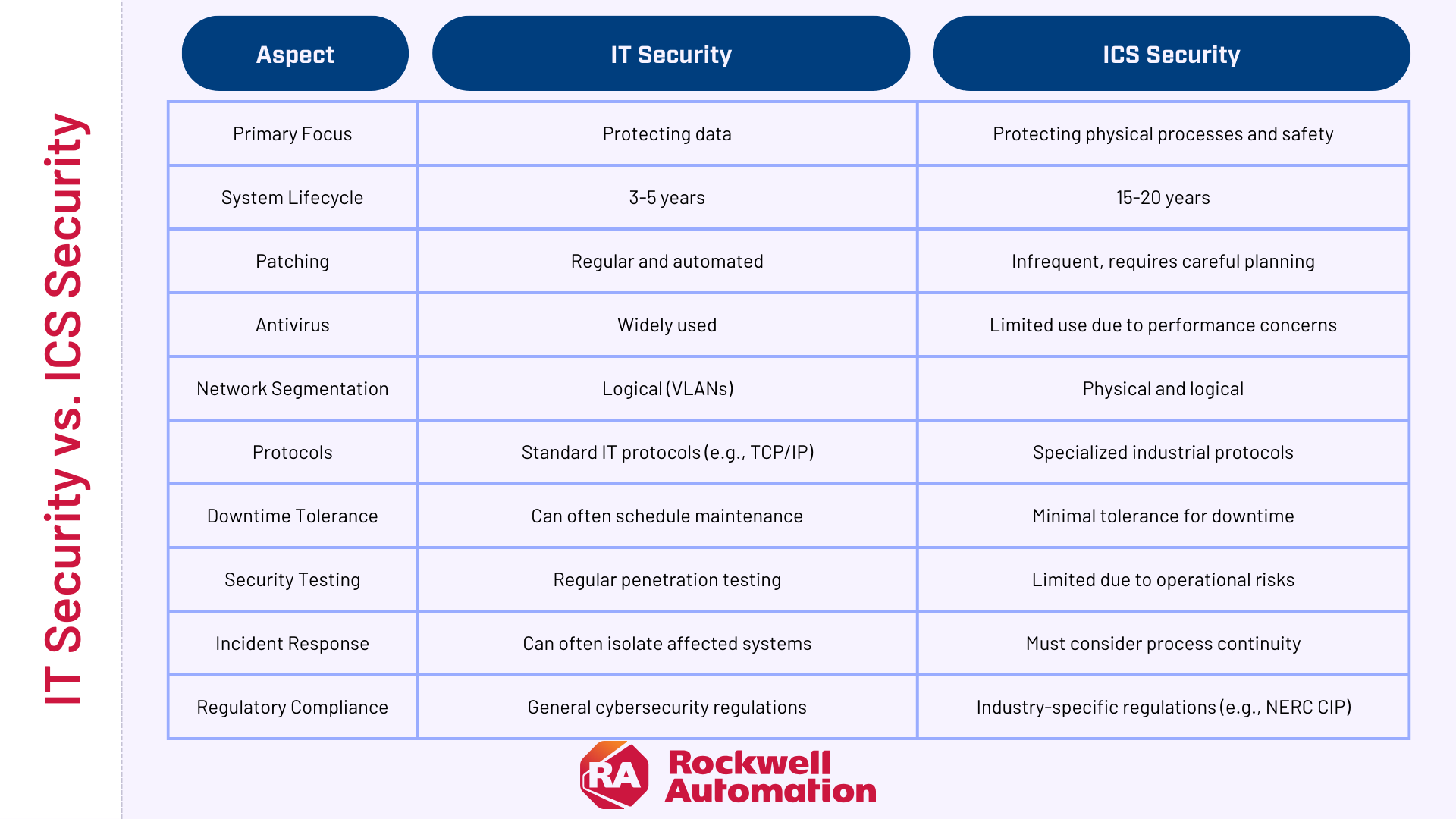
How Does ICS Security Differ from IT Security?
Your ICS is the backbone of your company’s operations. They manage everything from power grids to manufacturing lines—and their smooth operation directly impacts your bottom line. While IT security focuses on data and networks, ICS security focuses on securing the physical processes that the systems control.
Unique Challenges of ICS Devices ICS environments often include legacy systems and specialized devices that pose unique security challenges:
- Many ICS devices run outdated operating systems (e.g., Windows XP) that no longer receive security updates.
- Embedded systems like PLCs (Programmable Logic Controllers) and RTUs (Remote Terminal Units) often lack built-in security features.
- ICS components typically have long lifecycles (15-20 years), making frequent updates or replacements impractical.