Industrial operations—ranging from vast factory floors to power plants, refineries, and water treatment sites—keep our modern world running 24/7. Over the last decade, many of these environments have intertwined their operational technology (OT) with enterprise networks, cloud services, and remote-access setups. This move boosts real-time data oversight, centralized coordination, and more efficient maintenance. But it also multiplies the risks, drawing the attention of ransomware operators, state-affiliated adversaries, and everyday cybercriminals to newly linked industrial systems.
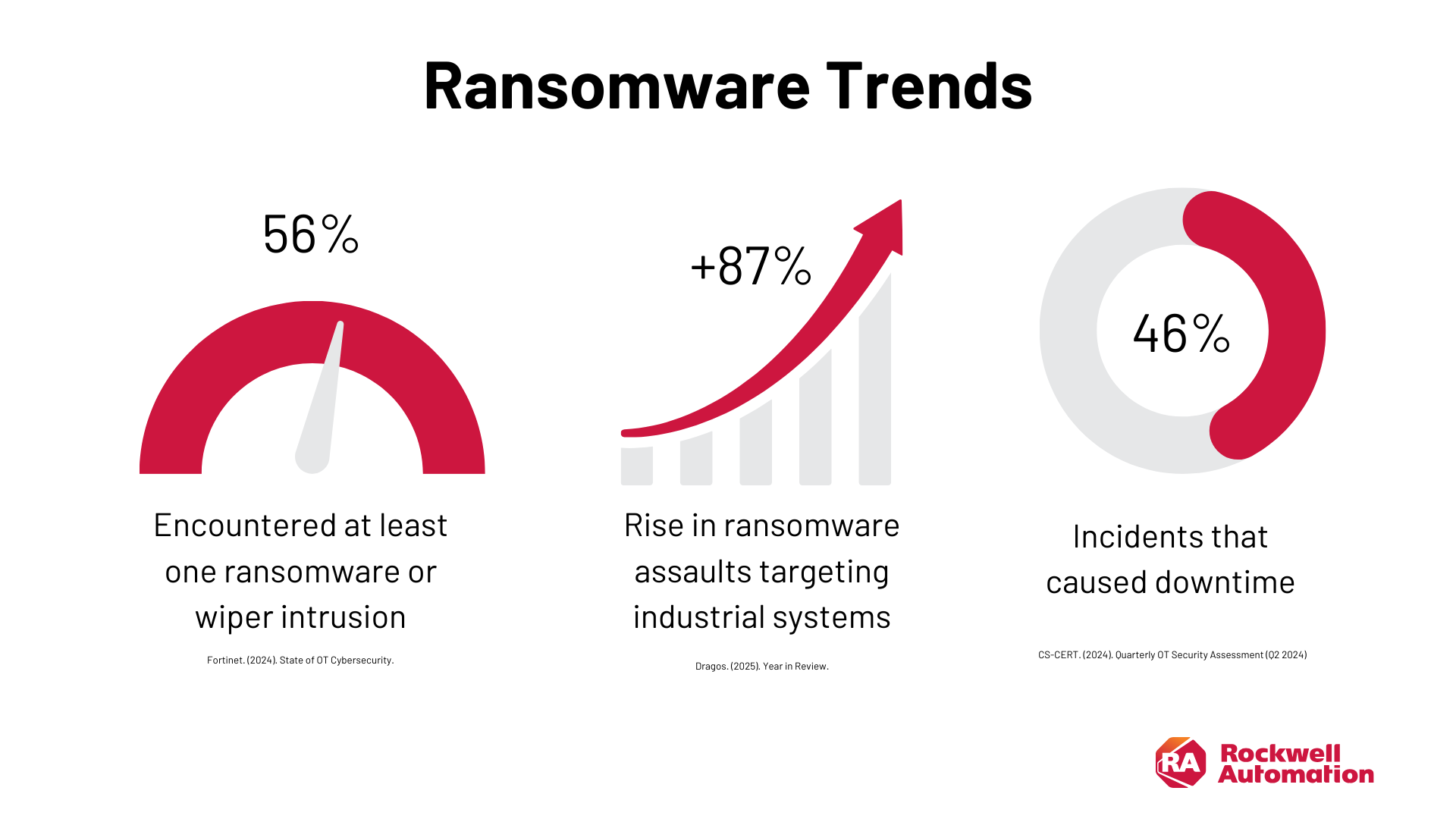
Industrial networks have seen a startling surge in malicious activity over the past year. Fortinet’s State of OT Cybersecurity 2024 reveals that 56 percent of OT organizations experienced at least one ransomware or wiper intrusion within the last 12 months. Around the same time, Dragos’ Year in Review 2025 documented an 87 percent rise in ransomware attacks directed at industrial systems—troublesome numbers for anyone operating critical infrastructure. And in Q2 of 2024, ICS-CERT reported that 46 percent of OT-related cyber incidents caused operational downtime. It’s hardly surprising that plant managers and security leaders remain wary—unaddressed gaps in interwoven OT environments can quickly derail production and drive up costs.
This guide offers a practical way to help defend OT systems, built around the six key pillars of the NIST Cybersecurity Framework—Identify, Protect, Detect, Respond, Recover, and Govern. You’ll find real examples, practical advice, and tried-and-true methods here, all aimed at helping OT professionals shift from reactive, crisis-driven methods to a more proactive (or preventive) resilient security stance—defending the industrial backbone that fuels our everyday lives.
The NIST Cybersecurity Framework: A Strategic Approach
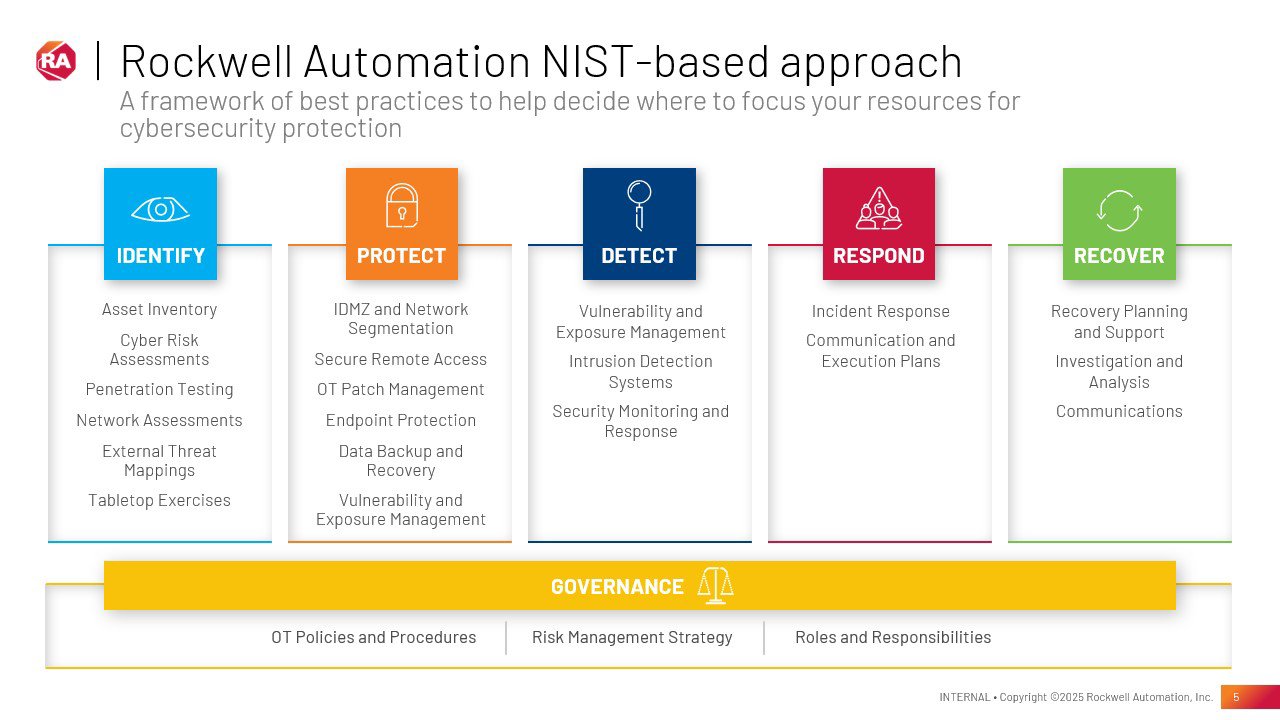
To combat escalating risks, countless organizations look to the NIST Cybersecurity Framework, which rests on six interrelated functions: Identify, Protect, Detect, Respond, Recover, and Govern.
Identify
You can’t protect what you can’t see. OT environments often feature everything from legacy machinery to cutting-edge sensors, each with its own vulnerabilities. Conducting regular audits and assembling a thorough, real-time asset inventory illuminates potential vulnerabilities. Once you know what’s out there, you can focus on the assets most vulnerable to threats.
Protect
Think of protection as fortifying a fortress. Multi-factor authentication, for instance, adds an extra wall around sensitive systems. Strict access controls limit who can tinker under the hood, and segmenting networks reduces the blast radius of any successful breach. Investing in these measures upfront is almost always cheaper—and far less chaotic—than scrambling to contain an unchecked cyber incident.
Detect
No matter how secure your perimeter, determined attackers may find a way in. This is where continuous monitoring and real-time alerts become pivotal. Tools that flag unusual traffic or unfamiliar user behavior give security teams the head start they need to investigate. Time is everything: the quicker you notice a problem; the sooner you can prevent it from spiraling out of control.
Respond
Sometimes, despite best efforts, cybercriminals still slip through. An incident response plan serves as your crisis blueprint. It outlines who makes decisions, how teams coordinate, and how you communicate with stakeholders—including employees, customers, and partners—so that confusion doesn’t amplify damage. A well-choreographed response can be the difference between a short disruption and a drawn-out catastrophe.
Recover
Getting back on track means more than rebooting a few machines. A thoughtful recovery plan goes deeper: it pinpoints how and why an attack succeeded, mends security gaps, and translates lessons learned into updated procedures. This introspection fortifies systems against the next cyber onslaught and helps restore confidence within the organization.
Govern
Strong governance acts as the cornerstone of OT security. Ask yourself: Who drafts policies, and who ensures those policies aren’t just ink on paper? By establishing formal oversight and assigning clear roles—like a chief information security officer or a dedicated team—leadership gains full visibility into daily operations. That clarity helps integrate cybersecurity objectives into broader strategic goals.
Building a resilient OT security posture isn’t just about shielding hardware or data. It’s about protecting the people who keep facilities humming and preserving the trust stakeholders place in your operations. By weaving the NIST Framework’s core principles into everyday workflows, organizations shift from playing defense after a breach to proactively thwarting threats before they take root.
NIST Category 1: IDENTIFY
Laying the Groundwork for Proactive Defense
In industrial contexts, many security lapses stem from the same fundamental oversight: failing to maintain an accurate, up-to-date view of the OT landscape. “Identify” in the NIST Cybersecurity Framework emphasizes the importance of understanding what you’re defending—machines, sensors, controllers, network pathways, and the data flows that keep everything running.
Why Visibility is Paramount
OT environments can host thousands of sensors, PLCs, drives, and field devices. Some of these components might be decades old and communicate via protocols that modern IT scanning tools do not parse well, such as Modbus RTU or Profibus. If these assets go unnoticed, they could be missing essential patches or still use default credentials, leaving the door wide open to attackers.
Lack of visibility also complicates incident response. When something goes wrong, precious time is wasted figuring out which equipment is at fault. Early detection is possible only if operators and security teams know what “normal” network and device behavior looks like.
Common Challenges to Achieving Visibility in OT Environments
- Age and Diversity of Systems: Legacy DCS (Distributed Control Systems), proprietary ICS hardware, and brand-new Industrial IoT solutions can coexist. This mosaic requires specialized discovery and monitoring tools.
- Protocol Complexity: Proprietary or uncommon industrial protocols won’t show up cleanly in a standard TCP/IP sweep. Tools like Wireshark can decode them, but consistent monitoring requires an ICS-aware platform.
- Resource Constraints: Some production systems cannot endure performance hits from active scans. Techniques must be carefully designed to avoid triggering process shutdowns.
Four Cornerstones of a Mature Identify Program
Comprehensive Asset Inventory
Spreadsheets and passive monitoring can only take you so far. If you want real security in industrial environments, you need full visibility—not just glimpses of network traffic. That’s where endpoint-based asset discovery comes in. By directly interacting with controllers, HMIs, and field devices, this method can uncover assets that might otherwise go unnoticed. Even devices that aren’t actively communicating on the network can pose risks, so identifying them is critical. But it’s not just about knowing what assets exist—it’s about understanding their full context.
Gathering deeper contextual data—such as device configurations, communication behaviors, user access patterns, and operational dependencies—allows security teams to move beyond basic inventory lists. A PLC with outdated firmware might seem like a high-risk asset on paper, but if it sits in an isolated, low-impact area, it may not require immediate remediation. On the other hand, a seemingly minor vulnerability on a device directly controlling a high-speed production line could have serious safety or financial consequences. By layering asset intelligence with real-world operational context, organizations can pinpoint vulnerabilities sooner, prioritize risk more effectively, and apply security controls where they matter most.
Network Topology & Data Flow Mapping
Visual diagrams and real-time maps of data flows create a blueprint of interdependencies. If an attacker compromises an HMI (Human-Machine Interface), you want an immediate sense of which PLCs could be affected. Mapping also helps plan segmentation strategies.
Vulnerability Tracking
ICS-specific vulnerabilities can linger for years if they’re not properly cataloged. Tech-enabled vulnerability assessment tied to your asset inventory flags known weaknesses. But without deeper context—such as exploitability, device criticality, and network exposure—organizations risk wasting time on low-impact fixes while missing the real threats. Remediation or mitigation steps should be prioritized based on a combination of vulnerability severity and operational impact.
Operational Criticality Rating
Rank each system or device by its importance to safety, production, or compliance. If a sensor malfunction on a chemical line could cause an environmental hazard, that sensor moves toward the top of your security checklist. This prioritization should go beyond just labeling devices as “critical” or “non-critical.” Understanding the operational role of each asset—how it connects to broader processes, what data it generates, and what failure would mean for production—enables security teams to focus on the threats that pose the greatest real-world risk.
Beyond “One-and-Done” Inventories
It’s tempting to do a detailed asset inventory once, put the data on a shelf, and forget about it until the next major project. However, modern manufacturing plants are in constant flux—new product lines get added, existing lines get reconfigured, and sensors get replaced. A device added by a contractor for a pilot test can remain connected indefinitely if nobody is monitoring. Continuous or scheduled scanning and thorough process documentation are essential for maintaining an accurate, risk-informed view.
Starting with the Identify function builds a strong foundation for every part of the NIST Framework. It’s difficult to protect, detect, or respond effectively when you lack a clear understanding of your environment. Detailed awareness of your OT environment is the compass by which you navigate emerging threats. Every time an asset is discovered, or a vulnerability is flagged, the rest of your security organization gains that much more clarity. Ultimately, the Identify stage can help you from being caught off-guard, which is a perilous situation in any real-time production system.
NIST Category 2: PROTECT
Delivering Uninterrupted Operations with Preventive Defenses
Once the industrial landscape is mapped and cataloged, the next question becomes: How do you build robust safeguards around your most critical assets? Many organizations look only to perimeter firewalls or antivirus tools. In complex OT settings, a more holistic layering of security measures is paramount. Intruders might arrive through remote access services, a maintenance laptop, a converged IT/OT data link, or a supplier’s compromised software update. A single line of defense simply cannot address the countless ways an attacker might enter or move laterally.
Defensive Depth in Industrial Systems
The “Protect” category deals with practical steps to keep attackers out of critical production layers, or at least severely limit their ability to cause widespread damage if they manage to break in. Intrusion attempts could focus on disabling an HMI, corrupting a logic controller’s firmware, or tampering with the historian database that logs production runs. Each potential target demands careful risk analysis and relevant controls.
Examples of Protective Measures
- Network Perimeter Protections: Classic perimeter firewalls, intrusion prevention systems (IPS), and content filters manage inbound and outbound data.
- Segmentation & Microsegmentation: Traditional zone-and-conduit models (based on the Purdue Model for ICS) can separate business-level systems from controls. Microsegmentation refines this further by isolating smaller subsets of devices or processes within their own security enclaves.
- Endpoint Protection & Hardening: Lightweight allowlisting or next-generation antivirus solutions for operator consoles. Restrict user privileges to reduce the risk of an attack pivoting from a single workstation to the entire network.
- Secure Configuration Management: Enforce rigorous access control lists (ACLs), incorporate role-based access control (RBAC) so only authorized individuals can modify configurations, and require multi-factor authentication (MFA) for stronger identity verification. Disable unused ports and services, remove default credentials, and automate configuration checks to maintain consistent security baselines.
Why Segmentation Is Critical for OT
Segmentation, often conflated with the simpler “air-gap” approach, is more nuanced than just blocking traffic from a corporate network. True segmentation requires deliberate architectural planning. You create distinct layers (for example, Level 2: local controllers, Level 3: site operations, Level 4: enterprise IT) with monitored conduits between them. Each layer is governed by firewalls or industrial demilitarized zones (IDMZ), limiting unauthorized movement.
Microsegmentation Benefits
- Damage Containment: If an attacker compromises a workstation in one cell, they can’t pivot laterally to sabotage other critical cells.
- Policy Customization: Different zones can have unique rules. For example, a safety instrumented system (SIS) zone may enforce the strictest communication parameters, while a maintenance zone might be more flexible.
- Zero Trust Alignment: Microsegmentation complements a Zero Trust mindset: never trust, always verify. It’s especially relevant for ICS networks that historically granted broad trust once you were inside the perimeter.
Real-Time Change Management
Factories are dynamic. Scheduled or unscheduled downtime occurs for repairs or upgrades. Over time, employees might attach new devices or open temporary communication paths for troubleshooting. These changes alter the security environment. A robust Protect strategy integrates real-time change management, verifying every addition or modification against established security policies. If a contractor tries to bypass the firewall for remote maintenance, automated alerts or manual approvals should be triggered before that channel is opened.
Continuous Patching and Configuration Hardening
OT systems commonly go unpatched for long stretches to prevent any disruption to ongoing processes. Unfortunately, attackers exploit this predictable gap. A layered patch management cycle, typically done in coordination with process engineers and maintenance windows, remains essential. Solutions like offline patch testing can verify that updates won’t disrupt production. Additionally, secure configuration practices must confirm that well-known vulnerabilities (for example, default admin passwords on PLCs) get remedied swiftly. Specialized ICS patch management solutions can schedule and distribute updates in ways that minimize operational risk.
The Move Toward Zero Trust in OT
Zero Trust in manufacturing is no longer hypothetical. Some advanced organizations deploy Zero Trust Architecture (ZTA) frameworks specifically adapted to ICS networks. They integrate continuous authentication and micro-authorization to confirm every device or user request. Because ICS protocols like Modbus or EtherNet/IP rarely incorporate strong authentication, wrapping these systems with a Zero Trust overlay can significantly reduce lateral movement risks.
Summarizing the Protective Layer
Protecting OT infrastructures requires a strategic blend of segmentation, endpoint defense, secure configuration, and alignment with recognized standards like ISA/IEC 62443. By weaving these practices together, facilities are better equipped to maintain operational continuity and avert catastrophes. Rather than fixating on perimeter fortifications alone, advanced ICS security demands a multi-layered architecture. This architecture can endure even if one defensive component fails, keeping essential processes alive and well.
NIST Category 3: DETECT
Stop Threats Early—Before They Cause Cascading Failures
Sophisticated attackers might lie undetected within an OT environment for extended periods, slowly testing which valves or PLCs they can control. Traditional IT intrusion detection solutions often miss ICS-specific signals, especially if they focus on Windows or Linux logs without an ICS-aware vantage point. The “Detect” function confirms that anomalies are noticed quickly enough to help prevent real damage.
24/7 Monitoring in an Always-On World
Most industrial plants run around the clock. Attackers exploit off-peak hours—nights, weekends, holidays—when staffing is minimal. A robust OT monitoring solution can’t take breaks. It should continually track network traffic, operational data, and user activity, raising alerts at any sign of malicious intent.
Network Traffic Analysis
Monitoring OT environments requires more than just watching network traffic. While specialized OT monitoring tools passively observe data flows for suspicious patterns, this approach alone leaves gaps—especially when attackers move laterally or target devices that don’t communicate frequently over the network. A more effective strategy combines network traffic analysis with endpoint monitoring to provide a full-spectrum view of potential threats.
A combined approach detects threats by analyzing both network activity and direct interactions with endpoints, identifying anomalies such as:
- Unusual Commands: A PLC suddenly receives instructions to vent pressure in an abnormal sequence—detected at both the network and device level.
- Unscheduled Changes: Configuration changes applied to a plant-floor device outside standard maintenance hours—visible via endpoint logging and security policies.
- Protocol Violations: Malformed Modbus or Profinet packets indicate that an attacker is experimenting with exploit payloads—detected through both network scanning and endpoint event logs.
By integrating endpoint security, operations teams gain deeper insight into attacks that may not generate obvious network traffic. Instead of relying solely on signature-based detection (matching known bad patterns), advanced security platforms use AI and machine learning to establish a baseline of “normal” behavior for both network traffic and device-level activity. Over weeks or months, they can quickly flag unexpected spikes, unauthorized configuration changes, or unusual process executions, reducing response time and improving overall security posture.
Endpoint Monitoring & Log Correlation
Additional detection layers include monitoring industrial HMIs, engineering workstations, and specialized SCADA servers. Correlating logs across these endpoints can catch subtle infiltration signs:
- Failed login attempts on a SCADA server, repeated across multiple operators, might suggest a brute force attack.
- Service restarts during unusual times, possibly indicating malware hooking into system processes.
- Overlapping time stamps between an intrusion attempt on the corporate domain controller and anomalies in the OT environment.
Integration with Security Information and Event Management (SIEM) solutions or extended detection and response (XDR) can help unify these alerts. However, standard SIEM solutions might not parse ICS logs properly unless they’re customized with ICS threat intelligence feeds and event parsing rules.
Real-Time Alerts and Response
Early detection is most valuable when it directly translates to prompt intervention. Automated workflows can isolate suspicious endpoints or block data to suspect IPs the moment an anomaly is confirmed. These enforcement actions shouldn’t be taken lightly—false positives in an ICS environment can halt production. But with well-tuned detection logic, the benefits (stopping real threats) far outweigh the risks.
Key Outcomes of Robust Detection
Reduced Dwell Time
The faster a plant can detect an intruder, the less time attackers have to pivot across different controllers, sabotage processes, or steal intellectual property.
Less Collateral Damage
Rapid isolation of compromised zones minimizes the need to shut down an entire facility.
Proactive Forensics
Because logs are aggregated and correlated, investigators can piece together the attack chain quickly, identify root causes, and enhance future protections.
Achieving Round-the-Clock Security Through Collaboration and Support
Have you ever had a sensor reading that made you do a double take? Sometimes it’s a random quirk; other times, it’s the first sign of a planned intrusion. Usually, it falls to a team of process engineers, control-room staff, and security professionals to separate the trivial glitches from the genuine emergencies. When teams share their observations—like arguing whether a temperature spike is normal maintenance or a warning sign—they sharpen their ability to act as a group. Cross-training builds on this by using everyday irregularities as practice runs to catch risks early.
If no one notices the warning signs early, small issues can escalate into major emergencies. In places where safety and productivity take center stage, brushing off a suspicious signal can lead to broken machinery, stalled workflows, or stealthy intrusions. But running a 24/7 in-house watch is no small feat—it drains budgets and wears down staff. That’s where outside or managed service partners can prove invaluable. They step in during off-hours or peak loads and can review odd spikes so that they do not go unchecked. By combining local know-how—from both IT and OT—with automated alerts, you build a sturdier line of defense than any single strategy could manage alone.
Ultimately, solid security isn’t about choosing people over technology or in-house teams over external help. It’s about weaving them all together—operators, engineers, cybersecurity specialists, and outsourced experts—so that emerging threats find no gaps to exploit.
NIST Category 4: RESPOND
Rapid Action to Contain and Neutralize Threats
Even well-fortified defenses can be penetrated by a stealthy or persistent attacker. The question then becomes: Does the organization know how to respond effectively? Many industrial firms postpone incident response (IR) planning. Then, when a breach occurs, they scramble to figure out which teams or external partners to call, and processes get improvised amid panic.
The Price of Unpreparedness
In regulated industries—pharmaceuticals, nuclear energy, or chemical processing—a security breach can have immediate compliance ramifications. Failing to respond properly may expose a company to legal penalties, environmental hazards, or health and safety incidents. The operational and financial toll can magnify if the response is delayed or disorganized, because the attacker has precious time to escalate privileges, exfiltrate data, or sabotage ICS components.
Fundamental Components of an OT-Focused Incident Response Plan
Clear Roles and Responsibilities
Identify who leads the IR process. Map out the responsibilities of production engineers, control-room staff, C-level executives, and IT/OT security teams. Different roles need distinct playbooks that detail exact protocols.
Communication Protocols
During an incident, system outages might affect email or VoIP phones. Alternate channels, such as encrypted messaging apps or radio communication, should be established in advance. External stakeholders—regulatory bodies, supply chain partners, local authorities—may also need to be notified under certain circumstances.
Pre-Written Playbooks
Structured workflows for different incident types (for example, ransomware, insider threat, DDoS on ICS servers) guide first responders. These playbooks include technical steps (like isolating infected machines) and business processes (like notifying critical vendors or shareholders).
Tabletop Drills & Exercises
Paper plans lose value if they aren’t tested in near-real scenarios. Simulation exercises using real ICS systems in a controlled environment can reveal hidden gaps: missing contact details, unpatched failover servers, or staff confusion over escalation procedures.
Rapid Containment Strategies
Once an incident is confirmed, swift containment is vital. This might involve:
- Network Segmentation Adjustments: Temporarily blocking traffic to certain subnets or restricting connections from suspect endpoints.
- Access Revocation: Pulling privileges from compromised accounts to halt further infiltration.
- Industrial DMZ Lockdown: If the threat seems to cross from IT to OT, quickly sever or drastically limit communication between these zones until the threat is neutralized.
The challenge lies in balancing containment with operational continuity. Halting a critical process abruptly can cause financial losses or safety concerns. Skilled responders coordinate with process control teams to avoid creating new hazards while curtailing the spread of the attack.
External Expertise and Partnerships
Some industrial organizations maintain in-house incident response capabilities, complete with ICS security experts. Others rely on specialized providers or consultancies. Prearranged service agreements, known as IR retainers, are common. An external partner well-versed in ICS/OT investigations can step in immediately with forensic tools and best practices honed from multiple engagements. The key is not to wait until you’re in crisis mode to evaluate potential service providers.
Learning From the Aftermath
Post-incident reviews serve as catalysts for improvement. Every detail—from initial compromise vector to final resolution—yields lessons. Perhaps an engineer used a weak VPN password or a certain vendor-supplied update process was vulnerable. Documenting these insights guides enhancements in the Identify, Protect, and Detect phases, closing the loop in the NIST lifecycle. A robust response mindset transforms painful incidents into opportunities for resilience.
NIST Category 5: RECOVER
Restoring Normalcy and Fortifying for the Future
After an incident response winds down, the last piece of the puzzle is recovery—getting everything back online, checking that systems remain uncompromised, and making sure the same path of attack can’t be used again. In OT environments, rushing or mishandling recovery can lead to fresh damage, or worse, actual physical hazards.
Unique OT Recovery Challenges
- Legacy Systems and OEM Dependencies: Some ICS components demand vendor-specific firmware or proprietary software to be fully restored. Without comprehensive backups or manufacturer support, bringing older hardware back to life becomes far trickier.
- Coordinating Software Versions and Configurations: Rolling a system back to an older backup can spark mismatches if other linked components stay updated. In many OT settings, patch levels have to match across the entire production chain so nothing breaks when processes start up again.
- Safety and Compliance Validation: Simply powering up the equipment might not be enough. You may need to recheck critical safety features, recalibrate sensors, or verify batch consistency to meet strict regulatory benchmarks.
Best Practices for a Robust OT Recovery Framework
Comprehensive and Tested Backups
Backup strategies must include configurations, firmware, operator interface files, and any specialized ICS application data. Merely backing up Windows OS images on an HMI is insufficient if the actual control project files aren’t saved. Periodically verify backup integrity by performing practice restores in an isolated test lab.
Cross-Functional Recovery Teams
The recovery process can’t be IT-led alone. OT engineers, safety personnel, quality assurance, and even vendor representatives must collaborate to verify each restored component is safe and operational. A lead coordinator ensures tasks are logically sequenced.
Incremental Restoration
Powering up everything at once can create conflicts or reawaken old vulnerabilities. A more measured approach is to bring systems online in stages, testing them first in a sandbox or partial-load environment. That way, if any hidden malware or configuration errors remain, you’ll spot them before they can spread across the entire operation.
Validation and Post-Recovery Testing
Once everything’s humming again, it’s time for acceptance tests that mirror real production. Check that data flows match baseline expectations, make sure safety instrumented systems (SIS) are still intact, and confirm that any newly applied patches haven’t introduced new glitches.
Ransomware: A Special Recovery Case
Ransomware typically encrypts files across multiple machines. In an OT environment, infiltration can cause HMI lockouts or manipulated logic code. Restoring from backups is often the only path forward—assuming your backups are intact and cannot be accessed or corrupted by the attackers. Some organizations keep offline “cold” backups explicitly for these scenarios, stored in physically separate facilities. It can be lifesaving to have a recent offline snapshot of your ICS environment to reinstall everything from scratch if necessary.
Resilience Beyond Crisis Mode
When an incident response wraps up, it’s wise to revisit the earlier phases of the NIST Framework. Did your monitoring tools catch the breach in time? Did segmentation actually limit its impact? Were older patches or default passwords making life too easy for attackers? Folding these takeaways into the ongoing Identify–Protect–Detect–Respond–Recover cycle keeps your security posture evolving rather than staying stuck.
In fields like life sciences or petrochemicals, a prolonged outage can harm more than the bottom line. If production stalls, medication shortages or energy disruptions might affect entire communities. A well-orchestrated recovery plan not only gets operations rolling again quickly, it also helps preserve public trust—helping prevent small hiccups from expanding into major crises.
NIST Category 6: GOVERN
For industrial operations, strong governance isn’t optional—it’s essential. Organizations don’t all follow the same roadmap; some use the NIST Cybersecurity Framework (CSF), while others lean on IEC 62443, ISO 27001, or a customized mix of best practices. The key is choosing a structure that fits your risk landscape and operational needs. No matter the framework, governance delivers accountability, defines clear roles, and aligns security efforts with business goals.
Good governance answers key questions: Who owns security policies? How are risks assessed? What’s the response plan for an incident? It also helps prioritize security investments based on real-world impact, making sure IT, OT, and leadership stay aligned.
Selecting the right framework isn’t about checking boxes—it’s about building a scalable, adaptable structure that grows with your organization. A well-implemented governance model makes it easier to manage risk, meet compliance requirements, and continuously improve security resilience.
Aligning Leadership and Operations
Many industrial environments involve separate IT and OT teams, plus outside vendors for critical hardware or software. A solid governance structure confirms that executives, plant managers, and security professionals all follow a common vision. This often includes official guidelines on who owns which ICS assets, how patch cycles should run, or which red flags require an incident response. Clear accountability spells out leadership responsibilities—maybe the CISO or OT Director—for big-picture security investment, incident reporting, or compliance.
Budget and Resource Allocation
Governance also handles the flow of both money and personnel. Each NIST function needs proper funding so that security measures don’t stall mid-implementation. If a facility requires specialized network segmentation or ICS-protocol awareness, for instance, governance bodies can green-light the necessary budget. They can also approve training programs so OT personnel can master new tools or processes.
Policy Reviews and Audit Mechanisms
Security policies and procedures need periodic checkups—often tied to recognized standards like ISA/IEC 62443 or ISO/IEC 27001. Internal or external audits can verify whether the organization’s approach to Identify, Protect, Detect, Respond, Recover, and Govern remains up to date. If those audits spot gaps—like outdated asset inventories or missing backups—governance steps in to drive corrections.
Bridging Communication Gaps
A well-thought-out governance model also closes the loop between executives and on-the-ground engineers. That might mean regular security updates in leadership meetings, cross-department tabletop drills, or a shared language for discussing security goals. Effective governance cuts across silos, making sure investments in one NIST phase (like advanced detection) are matched by staff training or robust incident response planning in another.
Outcomes of Effective Governance
When governance is on point, each NIST function benefits:
- Identify: Leaders keep asset lists accurate and confirm vulnerability scans happen regularly.
- Protect: Organizational buy-in and approved budgets pave the way for microsegmentation, patch management, and zero-trust initiatives.
- Detect: Management invests in ICS-aware threat monitoring and real-time alert systems.
- Respond: Clear authority structures mean incident that playbooks get followed, with top-level support for decisive containment.
- Recover: Documented recovery steps, assigned roles, and proper funding enable a fast return to normal operations, plus a chance to learn from what went wrong.
In short, governance is the glue that holds the NIST Framework together in OT contexts. By clarifying accountability, securing resources, and streamlining communication, it confirms that security isn’t just tacked on at the last minute but is woven into everyday operations—helping protect critical processes, fostering a culture of awareness, and keeping business goals in sight.
Invest Now to Build Resilience and Reduce Disruptions
Industrial operations thrive on streamlined workflows. If those workflows seize up, it’s not just profits at stake—worker safety and brand reputation can also take a hit. Safeguarding OT requires more than quick fixes; it demands meaningful commitment and alignment with proven frameworks like NIST. Each function—Identify, Protect, Detect, Respond, Recover, Govern—helps your organization stay one step ahead of an ever-evolving threat landscape. By adopting a complete strategy, you can handle attacks more smoothly and keep essential processes humming.
Why Holistic Measures Matter
People Are Part of the Perimeter
Firewalls and detection tools can only do so much. If employees and contractors don’t recognize phishing emails or grasp the need for strong passwords, attackers can slip right in. A proactive culture—one that rewards rapid reporting of odd behavior—often catches threats before the tech does.
Technologies Demand Careful Integration
In OT settings, older protocols and real-time demands make simply dropping in standard IT security solutions risky. Any new tool should be tested for ICS compatibility and rolled out in a way that doesn’t disrupt production.
Continuous Audits and Drills
Attackers never rest, so security teams can’t afford to either. Tabletop exercises, red-team engagements, and regular network assessments keep organizations a step ahead. These proactive tactics pull NIST’s concepts from theory into daily routines.
Global Interconnectedness
One vulnerable link within your supply chain—like a subcontractor or distributor—can ripple through data connections, vendor portals, or shared platforms—hitting everyone involved. An effective ICS security plan extends to all remote suppliers and partners, requiring concerted efforts across multiple sites.
Bridging Gaps with Expert Guidance
Many organizations gain enormous value from outside OT security experts who truly understand legacy PLCs, zero-trust principles, and how to implement new solutions with minimal downtime. But that’s only part of the story: these specialists can also boost overall readiness by crafting thorough IR playbooks, running scenario-based tabletop drills, and keeping a 24/7 emergency retainer on standby.
Around-the-clock monitoring is another core piece: if something goes awry, these experts have the ability to respond right away, before a minor glitch grows into a major crisis. Pull all of this together—tailored planning, real-world drills, non-stop oversight, and well-tuned zero-trust methods—and you end up with a security approach that protects what matters most without derailing daily operations.
Culture: The True Linchpin of OT Security
Even the best tools and processes won’t guarantee security if the culture doesn’t support them. In a workplace that treats cybersecurity as seriously as physical safety, suspicious network behavior or a rogue USB drive gets reported right away. If employees fear backlash, though, they might stay quiet—giving intruders a free pass. On the other hand, a culture that encourages proactive alerts prompts immediate reporting, fosters collaboration, and invests in staff’s security skills.
Leaders set the tone by assigning serious cybersecurity budgets, confirming employees receive up-to-date training, and framing downtime from a breach not as an “IT problem” but a bottom-line threat. Frequent executive updates on security posture—and incentives for spotting or preventing issues—shift the atmosphere from mere compliance to genuine engagement.
Counting the Long-Term Advantages
Sustained Uptime
A smoothly running production line safeguards revenue, strengthens brand image, and cements partnerships.
Regulatory Compliance
Strong security can satisfy auditors, minimize legal exposure, and streamline certifications—especially in heavily regulated sectors.
Innovation Enablement
As IoT, AI, and advanced robotics become standard in factories, a robust security foundation enables them to operate safely and efficiently.
Competitive Edge
In a supply chain riddled with vulnerabilities, a hardened ICS environment can position you as a trusted partner in cautious markets.
Implementing the NIST Framework isn’t about checking boxes. It’s a practical approach that acknowledges real risks in industrial settings. By systematically applying Identify, Protect, Detect, Respond, Recover, and Govern, organizations cultivate a security culture that keeps pace with shifting threats and aligns with operational goals.
Moving Forward
Achieving this level of resilience demands time, resources, and genuine leadership buy-in—but the returns are major. Rather than letting the next breach catch your organization off guard, you can maintain nonstop operations, safeguard your reputation, and reliably serve customers and partners.
If you’re ready to go beyond patchwork fixes, consider partnering with cybersecurity experts who understand both IT and OT. They can design approaches that match your operational needs, manage risk, and help keep everything flexible and secure. It’s never too early—or too late—to invest in a future where cyber threats are a manageable blip instead of a full-blown crisis.
Published April 4, 2025
You may also be interested in

