Automating Remediation: Streamlining the Patching Process
The task of deploying patches or compensating controls is often labor-intensive, involving the identification of target systems, configuring patch deployment, and troubleshooting failures. Consider a threat like BlueKeep, where files are pre-loaded onto targeted systems in preparation. A nimble OT security team could then strategically plan the order of patch updates, guided by the detailed asset profiles. This planning could consider factors such as the asset’s location or criticality.
Envision further a patch management system that bypasses the initial scanning phase, having already identified the assets needing patches. This system could facilitate remote or in-person installations, verifying their success and updating the global dashboard in real time.
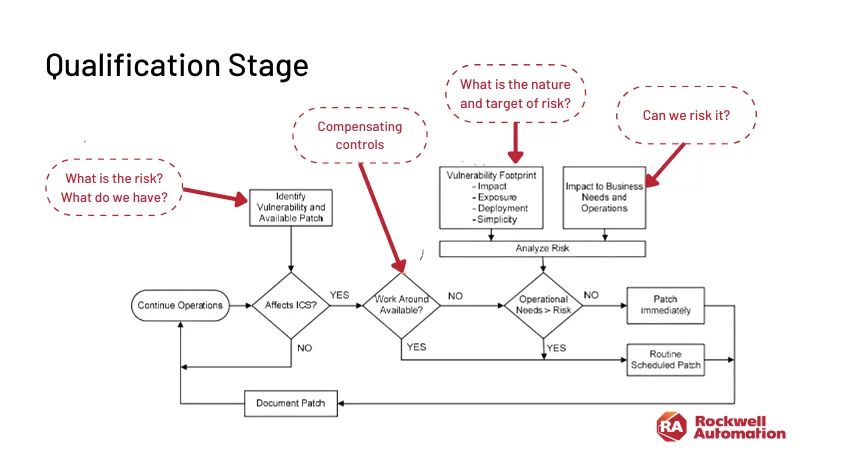
Compensating Controls: The Alternative When Patching Isn’t Feasible
For high-risk assets that cannot be patched immediately, the creation of ad-hoc compensating controls becomes a pivotal strategy. An example includes disabling remote desktop services or guest accounts in light of a critical vulnerability. This may drastically reduce immediate risks and buy time for patch preparation.
Bottom line: Compensating controls in OT environments are not merely stop-gap measures but integral components of a well-rounded patch management strategy.
Compensating Controls: A Vital Layer in OT Cybersecurity
Defining and Implementing Compensation Controls in OT Security
Think of compensating controls like a multi-layered defense system that’s deployed when direct solutions are not viable or could harm critical infrastructure with uptime requirements.
On the simpler side, we have actions such as application allowlisting and ensuring antivirus software is always updated. Moving towards more complex measures, there’s endpoint management—keeping a vigilant eye on each network-connected device for security vulnerabilities, and system hardening—which involves reinforcing the defenses of individual systems against potential threats. These compensating controls are crucial because they give us the flexibility and strength to bolster our OT security against various types of cyber risks.
Types of Compensating Controls in OT Security
Compensating controls aren’t fallback options, but proactive measures to strengthen defenses and address vulnerabilities. Let’s break down their scope.
Endpoint Management
Endpoint management involves meticulously monitoring and managing endpoint devices. The aim is to keep these devices updated and protected against known vulnerabilities, verifying they only have required access.
Why it matters: Endpoints are some of the weakest links in OT networks. Protecting these devices can reduce opportunities for attackers to access your critical systems.
You can implement this type of compensating control by:
- Keeping an inventory of all hardware and software endpoint devices
- Allowing only approved applications to run on the endpoints
- Using tools to maintain compliance and implementing strict configuration baselines for endpoints
- Collecting logs from endpoints to identify suspicious activity
- Deploying passive scanning tools to further identify vulnerabilities
System Hardening
System hardening involves strengthening the systems to make them more resilient to cyberattacks.
Why it matters: Hardening can make systems more resistant to exploits and malware.
You can implement system hardening by:
- Developing the minimum security requirements for baseline configurations for your OT systems
- Disabling services not required for system operation
- Closing unused network ports
- Granting users the minimal necessary access
- Conducting regular security audits to identify vulnerabilities and ensure requirements
Network Segmentation
Network segmentation is a defense in depth strategy that isolates critical systems by dividing the network into distinct segments.
Why it matters: Segmentation helps protect systems by containing breaches and limiting the damages caused by them.
You can implement network segmentation by:
- Identifying your most critical control and safety systems within your OT network
- Using firewalls and VLANs to create separate network segments
- Implementing strict access control policies between segments
- Monitoring traffic between segments regularly to detect suspicious activity
User Account and Access Control
User account and access control regularly checks and adjusts user access rights through measures like multi-factor authentication (MFA) and regular access reviews.
Why it matters: Unauthorized access can lead to data breaches and system disruptions. By implementing and maintaining effective access control, organizations can lower their risk and help protect themselves from insider threats and external attacks
You can implement user account and access control by:
- Requiring regular password changes
- Implementing MFA for all critical systems and accounts
- Assigning user access rights based on roles and responsibilities
- Using centralized identity management systems to oversee user access
Regular Backups and Data Encryption
Regular backups and data encryption are just like they sound: They consistently backup data and encrypt it.
Why it matters: Backups allow you to restore systems and data after a cyberattack, while encryption helps protect sensitive data from unauthorized access.
You can implement regular backups and data encryption by:
- Confirming the most critical data that needs to be backed up
- Automating backups on a regular schedule
- Storing backups offline or in a secure, separate network segment
- Encrypting all in-progress or resting sensitive data
- Conducting regular backup tests
Proactive and Situational Use of Compensating Controls
It’s important to deploy controls before a threat arises (proactively) and in response to specific situations (reactively). For instance, routine system checks might reveal dormant admin accounts or outdated software, which are vulnerabilities that can be mitigated through compensating controls.
Real-World Example: The BlueKeep Vulnerability Response
Imagine a scenario where a cybersecurity risk similar to the BlueKeep vulnerability emerges. For those unfamiliar, BlueKeep was a significant security vulnerability discovered in Microsoft’s Remote Desktop Protocol, posing a serious risk to unpatched systems by potentially allowing unauthorized access.
Now, let’s walk through how a prepared team could effectively handle an OT security incident response, illustrating the strategic use of compensating controls and proactive patch management:
Proactive Preparation for Emergent Risks
- Pre-Loading Patch Files: Suppose a new risk akin to BlueKeep is identified. Your first step could be to pre-load the necessary patch files onto all target systems. This preloading doesn’t mean immediate action, but it does prepare you for swift deployment.
- Strategic Patch Deployment: Imagine your OT security team, agile and informed, assessing which industrial systems to update first. This decision is based on a range of factors from your robust asset profiles, like the location of the assets or their criticality.
- Advanced Patch Management Technology: Now, envision a scenario where your patch management technology is so advanced that it doesn’t require a preliminary scan. Instead, it has already identified which assets are in the scope of the new patch. As you deploy these patches, whether remotely for low-risk assets or in person for high-risk ones, the technology verifies each patch’s success and updates your global dashboard in real time.
Implementing Compensating Controls for High-Risk Assets
But what about those high-risk assets you can’t patch immediately? This is where compensating controls come into play.
- Ad-Hoc Measures for Immediate Risk Reduction: For a vulnerability like BlueKeep, you might disable remote desktop services or guest accounts on these high-risk assets. This simple yet effective action can significantly reduce the immediate risk, buying time for a more comprehensive patching strategy.
- Fallback Actions When Patching Isn’t an Option: These compensating controls act as critical fallback actions. They’re not just stop-gap measures; they’re strategic choices that can allow you to maintain security even when immediate patching isn’t feasible.
By integrating these proactive and strategic approaches, your OT security team becomes capable of not just reacting to threats, but anticipating and preparing for them, bolstering the resilience and continuity of your operations in the face of potential cybersecurity challenges.”
Compensating Controls: A Key to Robust Cybersecurity
The strategy behind employing compensating controls is not merely a reactive stance to threats—it’s a proactive philosophy that complements traditional patching methods. These controls allow for an adaptable approach to securing OT systems, where understanding the network’s layout and each asset’s role informs the application of both patching and compensating controls. This method isn’t just about dealing with threats as they come; it’s about anticipating and preparing for them. The integration of these controls into your cybersecurity framework enhances resilience and helps protect critical infrastructure, helping to maintain operational continuity against a backdrop of evolving cyber threats.