LDAP
For LDAP, Provide the following details:
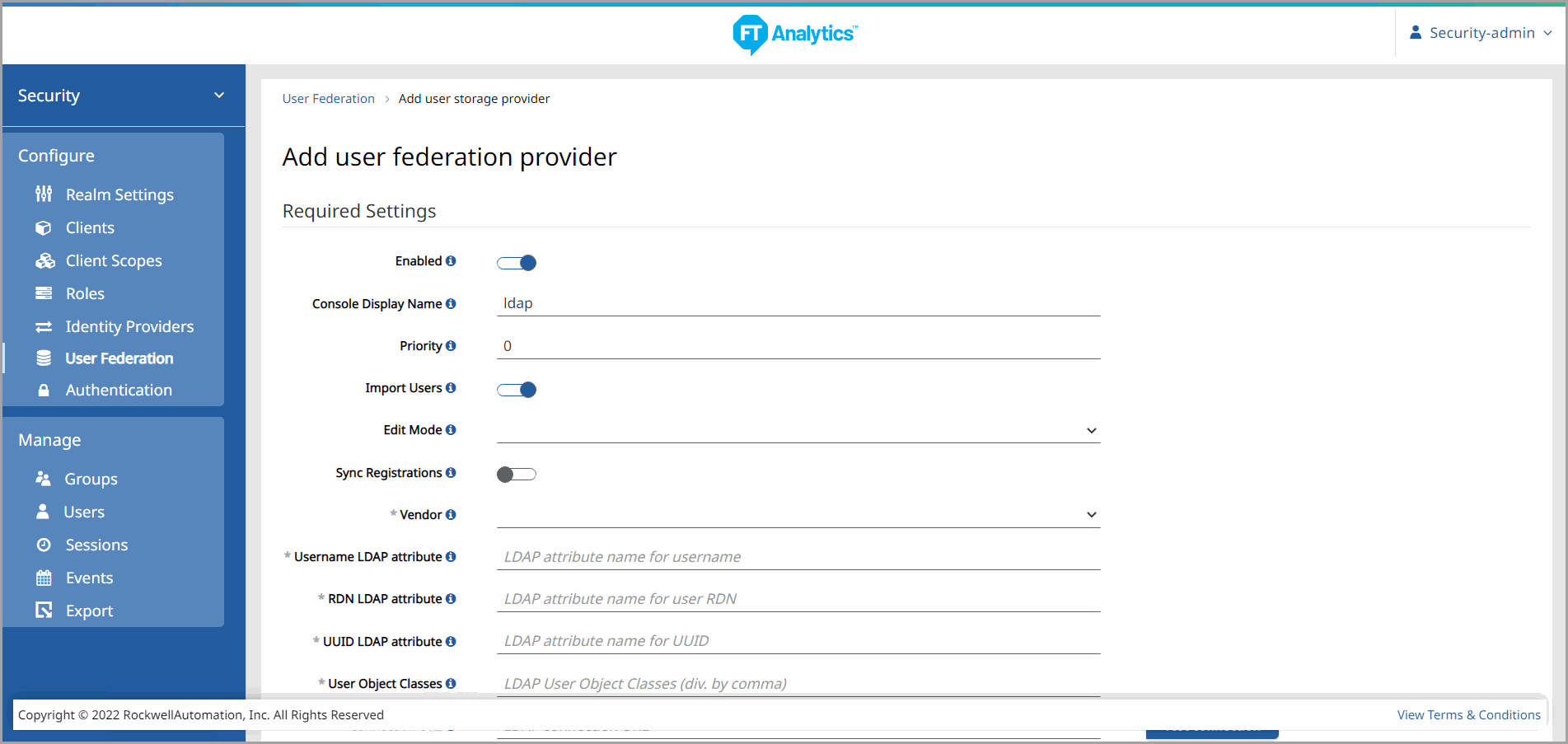
- Enabled - Toggle must be set to ON, if disabled Kerberos will not be considered for queries and imported Users will be disabled and read only until it is enabled.
- Console Display Name - The display name of the provider when linked in the Admin Console.
- Priority - Priority of the provider when performing a User search. This section is not applicable for LDAP.
- Import Users - Enable if you would like LDAP users to be imported into the Analytics Security Provider database and synced via the configured sync policies.
- Edit Mode - Select one of the following from the drop-down list.
- READ_ONLY - read only LDAP store.
- WRITABLE - data will be synced back to LDAP on demand.
- UNSYNCED - User data will be imported, but not synced back to LDAP.
- Sync Registrations - Enable if you would like to sync newly created Users from the Analytics Security Provider to the LDAP store. Priority will effect which provider is chosen to sync the new User.
- Vendor - Choose the LDAP vendor (provider) from the drop-down list.
- Username LDAP attribute - Enter the name of the LDAP attribute which will be mapped as the Analytics Security Provider username. The attribute should be filled for all LDAP User records you want to import from LDAP to the Analytics Security Provider.
NOTE:
For many LDAP server vendors it can be ‘uid’. For Active Directory, it can be LDAP ‘sAMAccountName’ or ‘cn’.
- RDN LDAP attribute – Enter the name of the LDAP attribute which is used as the RDN of the typical User DN.
NOTE:
Usually it is the same as the username LDAP attribute. However, it is not required.
- UUID LDAP attribute – Name of LDAP attribute, which is used as unique object identifier (UUID) for objects in LDAP. For many LDAP server vendors it's 'entryUUID' however some are different. For example, for Active directory it should be 'objectGUID'. If your LDAP server really doesn't support the notion of UUID, you can use any other attribute, which is supposed to be unique among LDAP users in tree. For example 'uid' or 'entryDN'.
- User Object Classes – Enter all the values of LDAP objectClass attribute for users in LDAP. All newly created Users will be written to LDAP with the object classes listed and existing LDAP user records are found if they contain the object classes listed.
NOTE:
The values should be divided by commas.
- Connection URL – Enter the connection URL to the LDAP server.
- Click [Test Connection] to validate the connection.
- Users DN – Enter the full Distinguishable Name of LDAP tree where your users are. This DN is parent of LDAP users. It could be for example 'ou=users,dc=example,dc=com' assuming that your typical user will have DN like 'uid=john,ou=users,dc=example,dc=com'
- Authentication Type – Enter the LDAP authentication type.
- None: Anonymous LDAP authentication.
- Simple: Bind credential and bind password authentication.
- Bind DN – Enter the Distinguishable Name of the LDAP Admin, which will be used by the Analytics Security Provider to access the LDAP server.
- Bind Credential – Enter the password of the LDAP Admin.
- Click [Test Authentication] to validate the authentication.
- Custom User LDAP Filter – Enter an additional LDAP filter to filter searched Users. This field may be left empty if it is not necessary.
NOTE:
The filter should start and end with parentheses ().
- Search Scope – Enter the scope level you would like the application to search from the following:
- One Level: only searches for Users in DNs specified by User DNs.
- Subtree: searches the whole subtree for Users.
- Validate Password Policy – Enable if you would like the Analytics Security Provider to validate the password with the realm password policy before updating it.
NOTE:
When using Federation there is the possibility that different rules are defined in multiple places. This setting controls whether the Analytics Security Provider password policy is used first.
- Use Truststore SPI – Specify whether the LDAP connection will use the truststore SPI with the truststore configured in standalone.xml/domain.xml.
- Always – It will always use it.
- Never – It will never use it.
- Only for LDAPS – It will use the truststore if your connection URL uses LDAPS.NOTE:Even if standalone.xml/domain.xml is not configured, the default Java cacerts or certificate specified by ‘java.net.ssl.trustStore’ property will be used.
- Connection Pooling – Enable if you would like the Analytics Security Provider to use connection pooling for accessing the LDAP server.
- Connection Timeout – Enter the LDAP connection timeout in milliseconds.
- Read Timeout – This setting defines how long to wait when making read requests to the LDAP or AD system. Read requests that take longer than the specified amount of time are considered failed requests. This value will be in milliseconds.
- Pagination: Select whether the LDAP server supports pagination or not.
- Kerberos Integration
- Allow Kerberos authentication - Enable or Disable HTTP authentication of users with SPNEGO or Kerberos tokens. The data about authenticated users will be provisioned from this LDAP server.
- Kerberos Realm - Name of Kerberos realm. For example: FOO.ORG
- Server Principal - Full name of server principal for HTTP service including server and domain name. For example: HTTP/host.foo.org@FOO.ORG
- KeyTab - Location of Kerberos KeyTab file containing the credentials of server principal. For example: /etc/krb5.keytab
- Debug - Enable or Disable debug logging to standard output for Krb5LoginModule.
- Use Kerberos For Password Authentication - Use Kerberos login module for authenticate username or password against Kerberos server instead of authenticating against LDAP server with Directory Service API.
- Sync Settings
- Batch Size – Enter the count of LDAP users to be imported from LDAP to the Analytics Security Provider within a single transaction.
- Periodic Full Sync – Enable if you would like to periodically sync LDAP users to the Analytics Security Provider.
- Periodic Changed Users Sync – Enable if you would like to periodically sync updates to Users or newly created LDAP users to the Analytics Security Provider.
- Cache Settings – Cache PolicyThe drop-down list provides the cache policy options for this storage provider.
- Default – the default settings for the global user cache.
- EVICT_DAILY – A time of day, which occurs every day that the User cache will be invalidated.
- EVICT_WEEKLY – A day of the week and time the cache will be invalidated.
- MAX_LIFESPAN – the time in milliseconds that will be the lifespan of a cache entry.
- NO_CACHE – It means that there is no caching.NOTE:This option may cause performance issues.User Federation
 User Federation (Continued)
User Federation (Continued)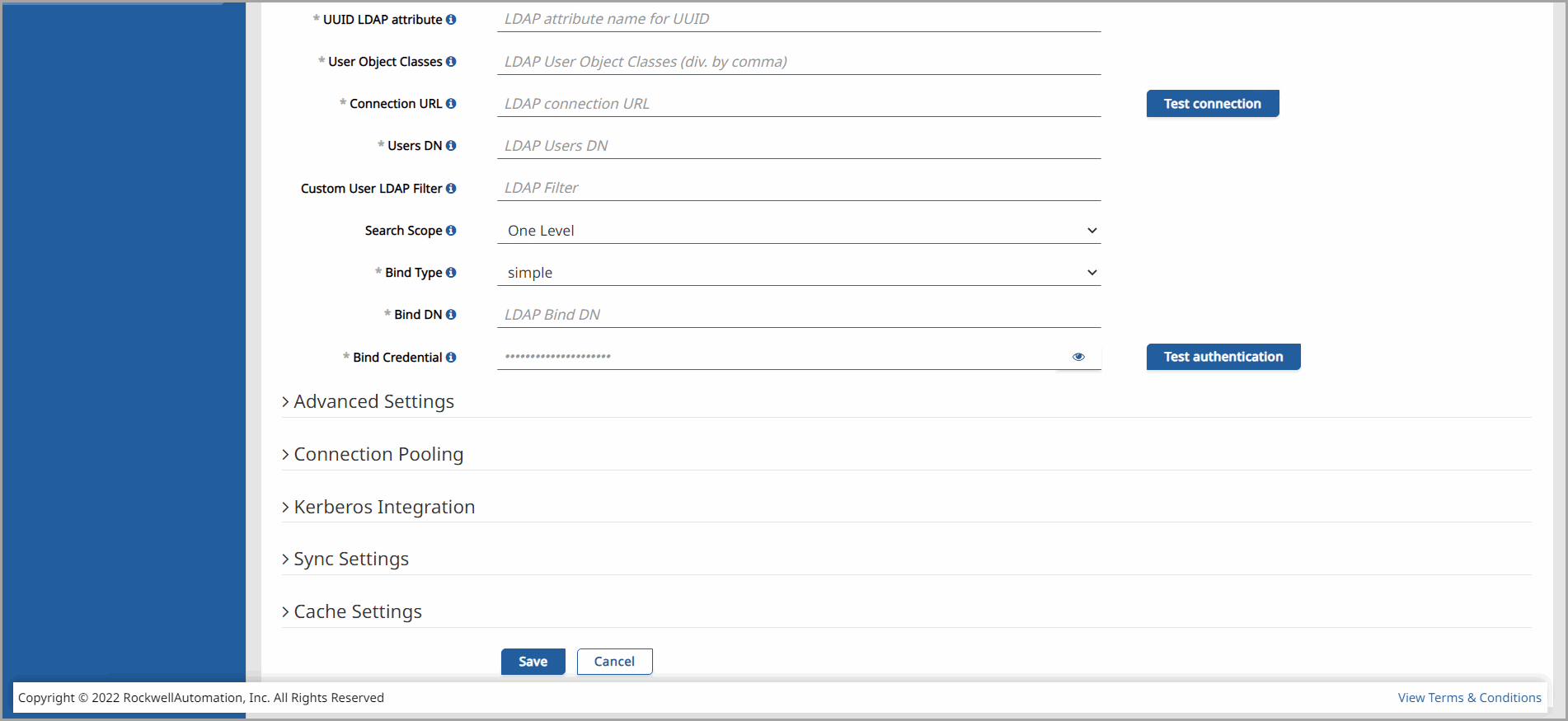
Click [Save] to update the LDAP configurations.
Click [Cancel] to discard any changes that were made.
Provide Feedback
