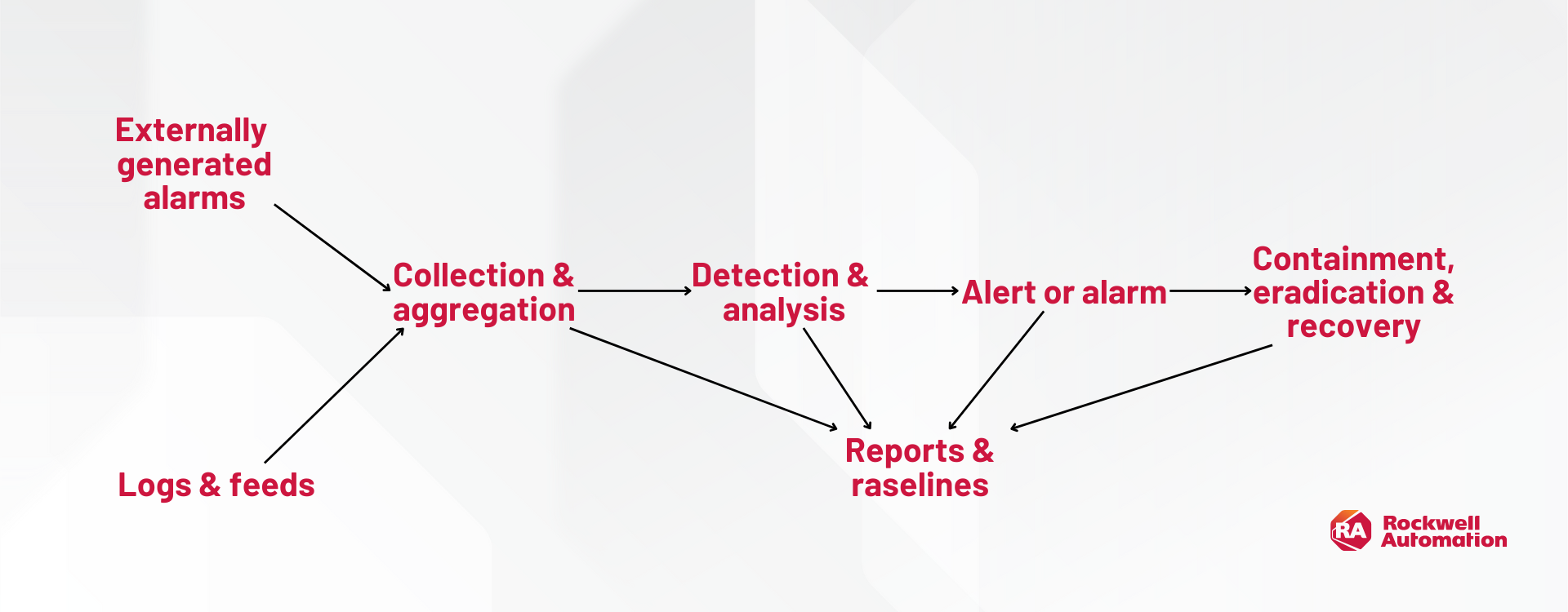
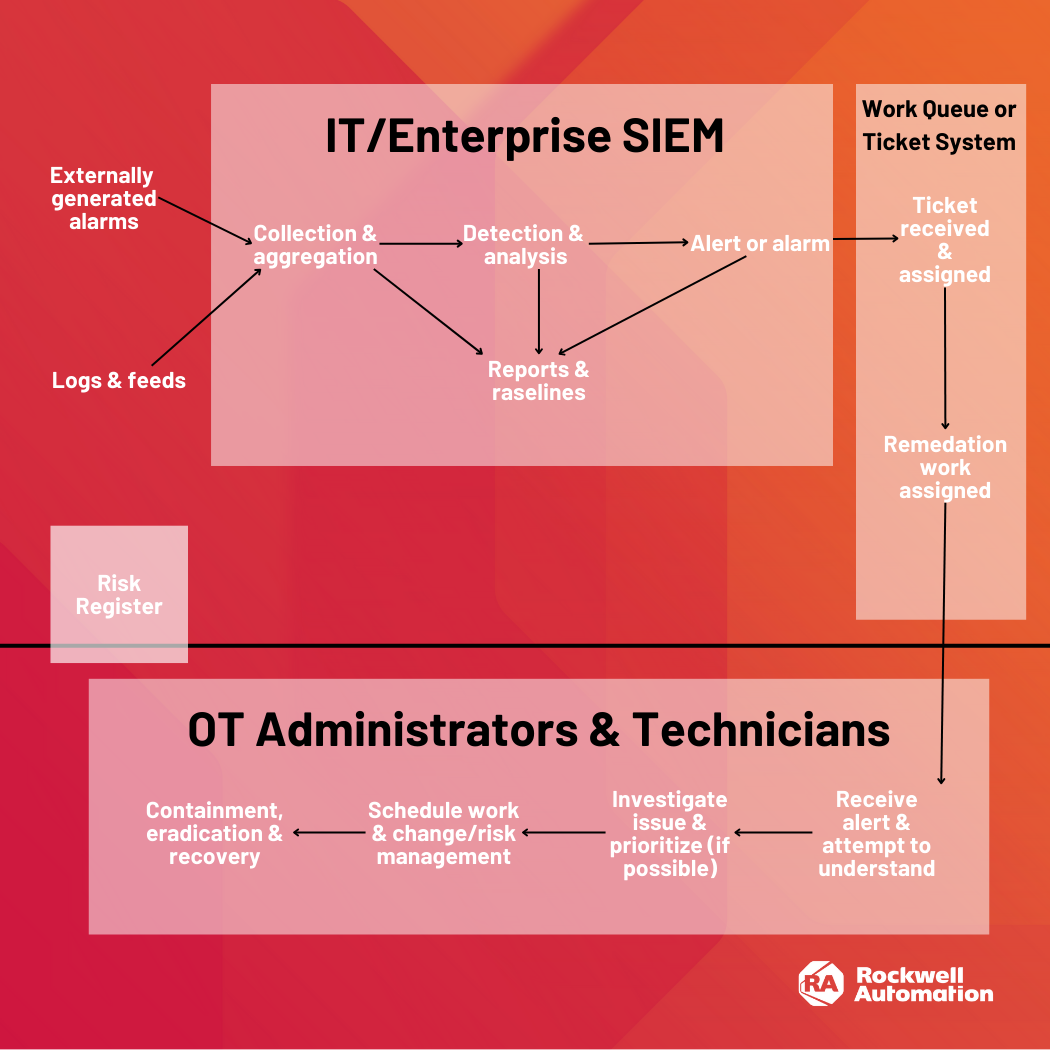
These triggers or thresholds are inherited from the generating application or system, leverage machine learning, statistics, or heuristics, but also human or framework-defined use cases.
Ultimately, a SIEM’s purpose is to receive messages (often in the format of Syslog, and Windows Event formats), make them available for cyber security functions, and alert upon them so security teams can effectively execute defined procedures and processes to manage the threat. This is best illustrated as an example:
Imagine you have a small or medium-sized business that has a convergent infrastructure. There are Windows systems used for accounts payable, as well as processing and distributing the shop floor’s orders and related tasks. Both of those functions are critical, but one is IT-related and the other is OT-related.
Now let us imagine that the individual at the helm of the accounts payable computer opens a phishing email, an attacker drops malware onto that system, and fortunately, that system’s anti-virus detects it while generating an alert.
This is a simple example, but in the case of commodity malware, and an organization managing their resources, it is advantageous to have their systems forward logs to a secure system for analytics, dispatch work and training. In this case, the malware was caught (for example, no massive ransomware attack), but the accounts payable person may need phishing awareness training or a visit from their manager.
What is the difference between an IT and an OT SIEM?
There is a good deal of debate around the need for an OT security operations center (SOC) to monitor, tune, and use the SIEM. There is a separate question on the value of an OT SIEM and what the difference would be from an IT SIEM.
SIEM Differences Between IT and OT
While both IT and OT SIEMs aggregate and analyze data, their focus and priorities differ significantly. In OT, the emphasis is on safety, reliability, and availability. This requires specialized data and analysis capabilities. Key differences include:
- Data: OT SIEMs incorporate process data, enabling deeper insights into operational anomalies.
- Analysis: IT typically deals with cyber threats that affect Confidentiality-Integrity-Availability, while OT works with Safety-Reliability-Productivity. An alert indicating a deviation in process parameters could signal a safety hazard or equipment malfunction, requiring immediate action. As you can imagine based on the convergence and interconnected nature of today’s networks, threats and systems/infrastructure overlap in many regards. Engineers and site operators must quickly tie asset information together with an event to triage a situation and execute a process (for example, to press the big red shutdown button vs. just reimage a system).
- Visibility: SIEM functions in IT environments are monitored in a central data warehouse, which is housed in a corporate data center. Visibility is limited to the security operations center. OT environments require on-site visibility for fast incident response.
- ROI: The IT SIEM is a pure security tool, generating value from reduced risk of cyberattack. An OT SIEM acts as an operating tool that can help predict equipment failures, reduce unplanned downtime, and save significant operational costs. For example, by monitoring vibration data from critical machinery, anomalies can be detected earlier, allowing for preventative maintenance. This includes use cases like:
- Predictive maintenance and resource monitoring
- Suddenly missing (offline) systems
- Transient asset spotting (potentially even rogue devices)
- Security alarms for traditional cyber threats or unauthorized accesses
- Unexpected system access or erroneous system behaviors
- Process failures, shutdown alerts, or manual alarm silencing
- Regulatory and compliance requirements
Regardless of the origin, there are overlapping SIEM use cases and cyber threats such as commodity malware, but the impacts and events affecting either side of the spectrum (IT vs. OT) are different the farther you traverse in either direction.
IT frequently faces threats from malware, phishing, data disclosures/breaches, and a variety of threats delivered straight from the Internet. For OT environments, threats are the compromise of specialized process control equipment, safety systems, and production lines. For both IT and OT, there are varying skill sets with different priorities based on the type of work performed and the events generated.
In IT, if an alert stating X user is doing Y, or Z malware alert has gone off, cybersecurity handling for those situations is reasonably understood. But in OT, a variety of proprietary vendors and technologies span decades, resulting in an overwhelming number of alarms or alerts for teams focused on keeping a facility operational (and safe).
What factors drive the need for an OT SIEM?
There is often a need for both IT and OT SIEM within one environment. In fact, in almost all industrial cyberattacks, the actor pivoted from IT into OT by first gaining a foothold on the IT side and traversing protections existing between the two environments.
A single view to oversee asset management, reporting, and SIEM functionality is required for effective cyber risk reduction across IT and OT.
The question that remains is how best to achieve that integrated view. When does it make sense to have an OT SIEM that provides specific data aggregation, analysis, incident response and reporting for OT and then forwards critical alerts and information into the enterprise SOC?
Those are questions where the approach and strategy are specific to the organization. For some organizations, a single SIEM, with no specific OT functionality makes sense. For others, having a robust OT SIEM will be critical.
Factors driving the need for SIEM
1. Complexity of OT process: Companies in the power sector, oil refineries, water treatment, etc. operate complex physical processes that require deep experience in the industrial control systems operations. To identify and analyze risks and response, the OT personnel need access to an OT SIEM to provide the detailed information that only they will understand in detail. The more complex the process, the more value derived from an OT SIEM.
2. Criticality of OT process: Many industrial organizations’ OT processes are the lifeblood of their organizations. Downtime, whether from a malicious attack or unintentional device disruption, costs a lot of money. As a result, monitoring for process variabilities, controls device behavior anomalies due to potential failure, new devices that may cause disruption, etc. add significant value. An OT SIEM provides this valuable information.
3. Network access/segmentation of OT infrastructure: The more separated the OT network from IT, the more valuable the OT SIEM becomes. As the dependence on local operations personnel to take actions increases, so does the value of an OT SIEM.
4. Compliance and regulations: In some industries such as the North American power industry, cyber security regulations such as NERC CIP require detailed OT data. This data may not make sense to include in an IT SIEM as they are more compliance oriented than providing the security analytics a SOC might use.
Challenges with issuing work orders from enterprise IT SIEM
The answer is not as straight-forward as it may seem on the surface, and the complexities are derived from the amount of legacy equipment, and amount of process control and regulations in the environment. After all, who would want to pollute their enterprise environment with X compliance bureaucracy & overhead? Probably few.